ISRM under ERM benefits
In recent years, it became the norm for information security risk management (ISRM) to be a cornerstone for enterprises and part of their overall enterprise risk management (ERM) efforts. Having ISRM as an integral part of ERM has many sound advantages. Here are few:
Direct information security efforts and provide scope and priorities
As a higher function, ERM refers to the enterprise strategic plan as a guide to set risk management priorities, scope, and objectives. ERM will then set the general criteria for risk appetite. What risks to accept and what risks to mitigate. What risks to take opportunity of (in case of positive risks). By being under ERM, ISRM will tune its efforts towards business objectives, making it efforts more valuable to the organization.
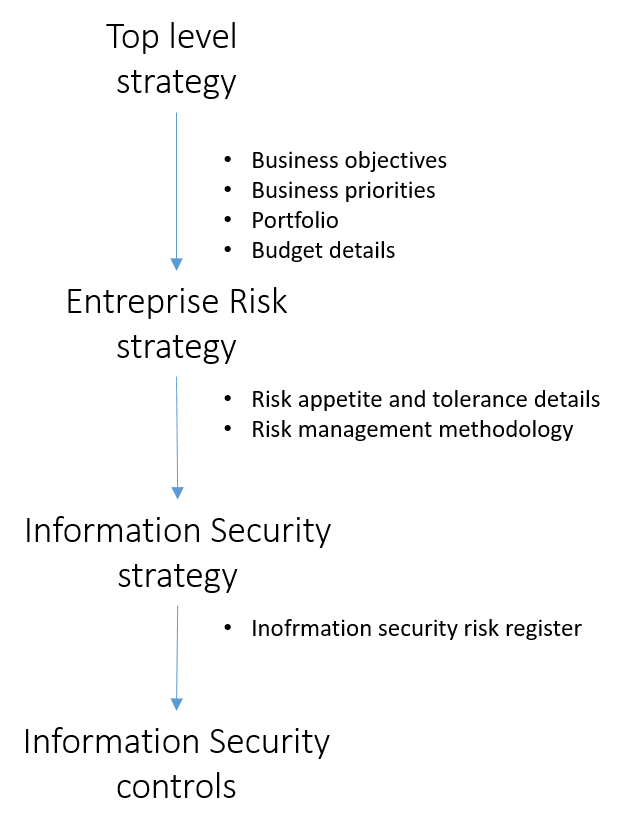
Optimize and streamline risk management processes
By using the same frameworks, risk assessment methodologies, scoring criteria, risk register format, workflows, ..etc, the required resources for risk management would be greatly reduced in comparison to having various risk functions work independently.
Unified measurement
Setting the metrics that evaluate the performance of ISRM controls normalized to business criteria rather than technical criteria. For example the measured reduction in unauthorized access can be translated to savings in non compliance penalties. This approach can align CCRM to business much better, help in prioritizing risks, and direct decisions on improvements to cyber controls.
Unified Reporting
When the output of ISRM is presented integral to an overall ERM executive report, in business language rather than technical language, it would be more useful to the decision makers. This is also allow the information security function to receive the higher level support needed.
Enable other business functions to have holistic risk analysis
In the digital age, it is rare to find any business process or function that does not depend to a certain extent on information technology. Thus, having ISRM addressed within the same framework of risks in other business areas is key to drawing a complete picture for these areas’ risks.
This was an incomplete list of the benefits of having information security risk managed under CRM. However, many enterprises adopted this approach not only establishing an integrated risk management process, they went further and applied the idea to their organizational structure. This is rooted to earlier days when IT security was introduced as a sub-function of IT. As IT security began to mature, and more broadly started to be called information security, it gradually became apparent that keeping it under IT is a conflict of interest as information security has a monitoring due diligence role over IT. Organizations started to separate information security in it’s own function and some, moved it under ERM for the benefits discussed above to be realised or even enforced. Although this has a lot of underlying merits to it, it didn’t come without, as sound, side effects, which are discussed next.
The Disadvantages Of Having Information Security Under Enterprise Risk Management
Information security is not only about risk management
While, as discussed earlier, Information security risk (including cyber risk) is an important undertaking, The information security function has much more to do. SOC and monitoring, incident management, threat intelligence, compliance, supplier management, application security, access management, and the list is long. Many of which are technological, each to a certain extent, and hence, may not be understood enough by ERM people. Having the information security function organized under risk management limits the information security function’s interactions with other functions and may distort their harmony with the rest of the organization.
IT – IS power balance
Information security is all about securing IT resources. They both understand technology and work closely together. There are two notable aspects to examine here: Information security needs to have some sort of upper hand over IT to ensure IT fullfils security requirements. On the other hand, IT is almost always a much larger department than information security. If information security is organized under ERM while IT is a more powerful distinct unit, information security’s influence on IT may get weaker and consequently severe issues may arise such as implementation delays, lengthy arguments, non compliance, and a host of other problems. The problem may be worse if IT is present in board meetings while information security isn’t.
Sound suppression
The absense of information security from board meetings reduces their contribution to the organization’s mission and their capture of points during board discussions that may be important to their concern and only they can capture. The issues they face can only be brought to the board’s table through the ERM proxy, which won’t portray a precise picture of information security subjects like a CISO would do.
Technology Language Barrier
Risk managers are not technology specialists like information security staff are. Being under the risk management umbrella means communicating everything to the risk manager. Risk managers may not be able to comprehend all the technical topics, or not to the required extent. The risk manager may not even be that interested in knowing about what they don’t undertand. One infromation security manager once told me when he talked once to his risk management boss about an issue, the answer was: “do not bring your shit here!”
The Solution
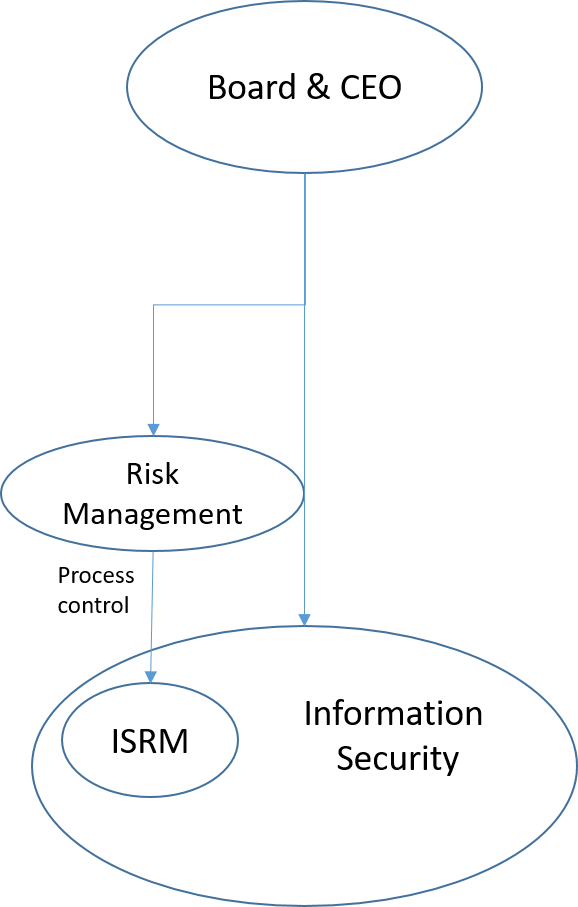
Information security definitly needs to have its risk management side work under the ERM umbrella. However the importance, diversity, and sensitivity of their role together with the technical nature of many of their undertakings necisate empowering the information security function in the organizational structure. Information security needs to be a distinct department under the CEO’s direct supervision with a reserved seat in the board meetings. For smaller organizations, if the size does not permit having a distinct unit with a CISO, the role that handles informatinon security should still be empowered and have a directe connection to the head of the organization.

Leave a Reply